Now Reading: Mastering Power Platform Security: A Complete Guide to Protecting Your CRM Data
-
01
Mastering Power Platform Security: A Complete Guide to Protecting Your CRM Data
Mastering Power Platform Security: A Complete Guide to Protecting Your CRM Data
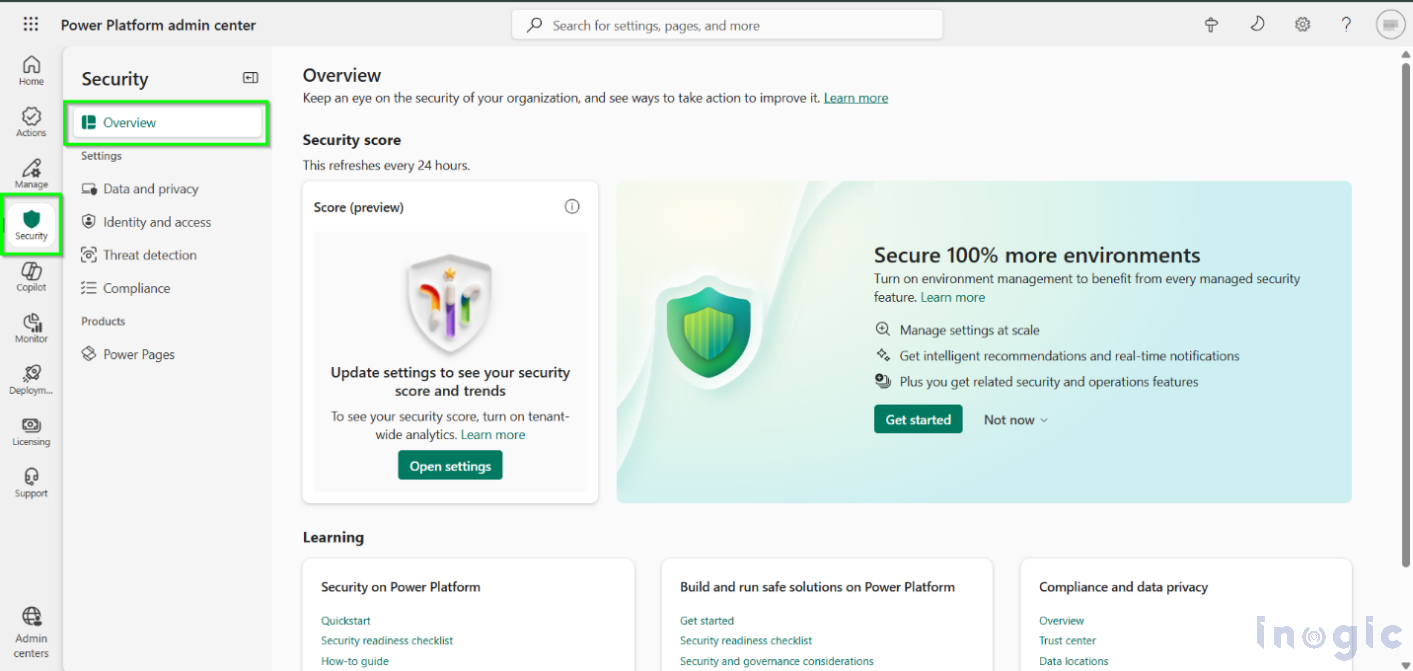
The Security Overview page in the Power Platform admin center serves as a centralized dashboard where you can monitor security, review your security score, and activate recommended policies. For CRM administrators managing Dynamics 365 and Power Platform environments, understanding these security features is essential to safeguarding your organization’s data.
Introduction
Microsoft Power Platform enables organizations to rapidly build apps, automate processes, and innovate without deep technical expertise. But with this flexibility comes a critical responsibility: protecting sensitive CRM data.
The Security Overview page gives administrators the visibility and tools needed to:
- Evaluate security posture
- Identify risks and vulnerabilities
- Enable Microsoft-recommended security features
- Strengthen governance across environments
All from one consolidated location.
Why Use the Power Platform Security Overview
Real-Life Scenario: CRM Data Protection
Imagine you’re a CRM administrator in an organization where employees have created numerous apps and flows connected to Dynamics 365 – many without proper governance. Some of these apps process customer data, and others interact with external systems. You lack visibility into:
- Who is accessing customer information
- Which apps have permissions to use sensitive records
- Whether data policies are preventing unauthorized data sharing
- Whether your environment meets compliance and security requirements
The Security Overview page solves these challenges by giving you:
- Immediate visibility into your security score
- Identification of gaps in your current security configuration
- Actionable, Microsoft-recommended steps to strengthen your overall security posture
This makes it a vital tool for ensuring that your CRM and Power Platform environments remain compliant, protected, and well-governed.
Step 1: How to Access & Use Power Platform Security Overview
To view your organization’s security score, you must first enable tenant-wide analytics.
After enabling it, the Security Overview page may take up to 24 hours to display your data. Until then, you might see the message “Calculating security score.”
Steps to enable tenant-wide analytics:
- Sign in to the Power Platform Admin Center.
- In the navigation pane, select Manage.
- Under the Manage section, choose Tenant Settings.
- On the Tenant settings page, select Analytics.
- In the Analytics pane, turn on Tenant-level analytics.
- Click Save.
Then, access the Security Overview:
You need one of the following Microsoft Entra ID roles:
- Power Platform Administrator
- Dynamics 365 Administrator
Steps to access the Security Overview Page:
- Sign in to the Power Platform admin center.
- In the navigation pane, select Security.
- Choose Overview, or explore related pages like Data Protection and Privacy, Identity and Access Management, or Compliance.
Note:
Only tenant administrators can view the security scorecard, see recommendations, or convert environments into Managed Environments.
Step 2: Understand Your Security Score
Your security score shows how secure your organization’s Power Platform and Dynamics 365 environments are.
It is displayed on a simple scale:
- Low (0–50)
- Medium (51–80)
- High (81–100)
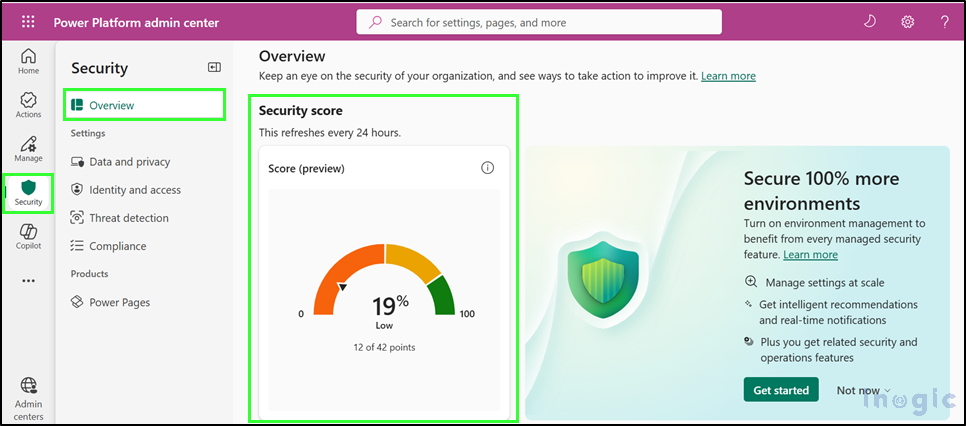
The more recommended security features you enable, the higher your score will be.
The score is calculated using this formula:
(Your score ÷ Total possible score) × 100
Each security feature has a specific score value based on its scope and how many resources it impacts.
For example, if you have:
- Tenant isolation enabled in 10 environments = 10 points
- IP firewall configured in 5 environments = 5 points
- Environment security groups set up in 3 environments = 3 points
- Total possible score = 30 points
Your security score would be:
(18 ÷ 30) × 100 = 60% (Medium)
Important: The security score updates every 24 hours, so any changes you make may not appear immediately.
Also, the total possible score may change as new security features are introduced, which can affect your overall percentage even if your current settings remain the same.
Step 3: Unlock Complete Security by Enabling Environment Management
To get the full advantage of Microsoft’s enhanced security controls, every environment in your tenant needs to be configured as a managed environment. With the latest update, admins now have a much easier way to view and convert unmanaged environments – helping organizations strengthen their overall security posture with minimal effort.
A Smarter Way to Manage Environments at Scale
Admins can now see exactly what percentage of environments are still unmanaged. From this view, you can convert multiple environments to managed status in just a few clicks – no complex setup required.
Here’s how the process works:
- Select Get started
- This opens the Get enhanced security features panel.
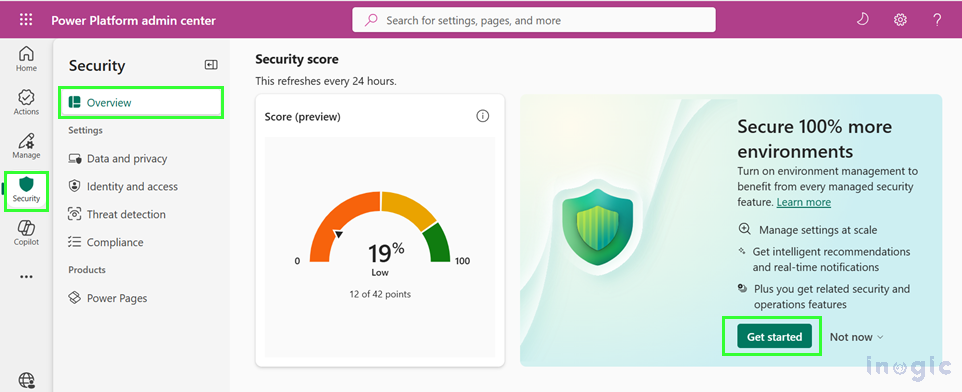
- Choose environments to convert
- Recommended environments tab highlights environments based on data volume, making it easier to prioritize.
- The All eligible environments tab lets you manually pick any environment you want to convert.
- Review the terms and conditions
Confirm your understanding before proceeding.
- Select Turn on environment management
This completes the conversion and activates the security features.
If you’re not ready to proceed, simply choose Not now. You can revisit the option at any time.
Why It Matters
Enabling environment management isn’t just another admin task – it’s a proactive step toward stronger, more consistent, and more reliable security across your entire organization. By converting environments to managed mode, you ensure that all your workspaces benefit from the full suite of Microsoft’s built-in governance, monitoring, and protection capabilities.
Taking this one step today helps safeguard your data, streamline compliance, and keep your tenant secure – now and in the future.
Step 4: Review and Implement Recommended Actions
The Security Overview page generates recommendations based on Microsoft best practices and common security conditions. The system identifies specific conditions that trigger recommendations:
| Feature | Scope | Condition that triggers recommendations |
| Administrator privileges | Environment | Environments that have more than 10 administrators |
| Auditing | Environment | Environments where auditing is turned off |
| Customer Lockbox | Tenant | Tenants where Customer Lockbox is turned on, but that have no Managed Environments |
| Client application access control | Environment | Environments where auditing is turned on and client application access control isn’t configured |
| Data policy | Tenant | No tenant-level policy is set. |
| Environments Azure Virtual Network | Environment | Environments that have no Virtual Network policy |
| Environment security group | Environment | Environments that have no security group |
| Guest access | Environment | Environments where restricted guest access is turned off |
| IP firewall | Environment | Environments where IP firewall isn’t configured |
| IP address-based cookie binding | Environment | Environments where IP address-based cookie binding isn’t configured |
| Sharing | Environment | Environments that have no sharing limit |
| Tenant isolation | Tenant | The tenant isolation setting is turned off. |
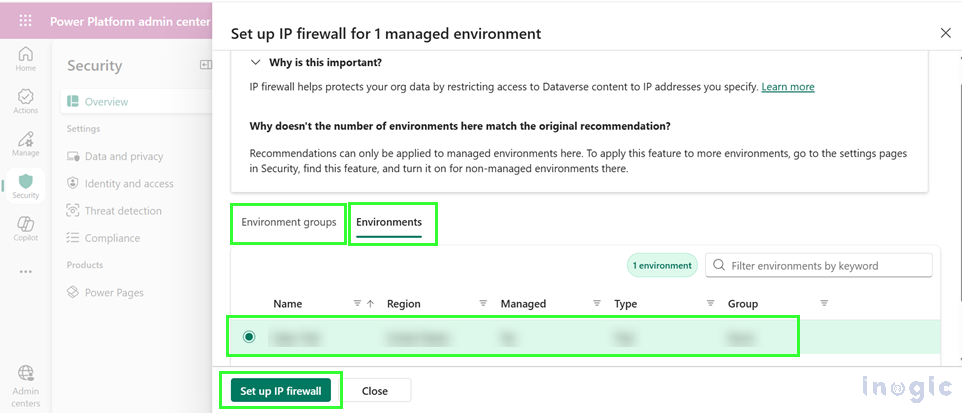
How to Act on Recommendations:
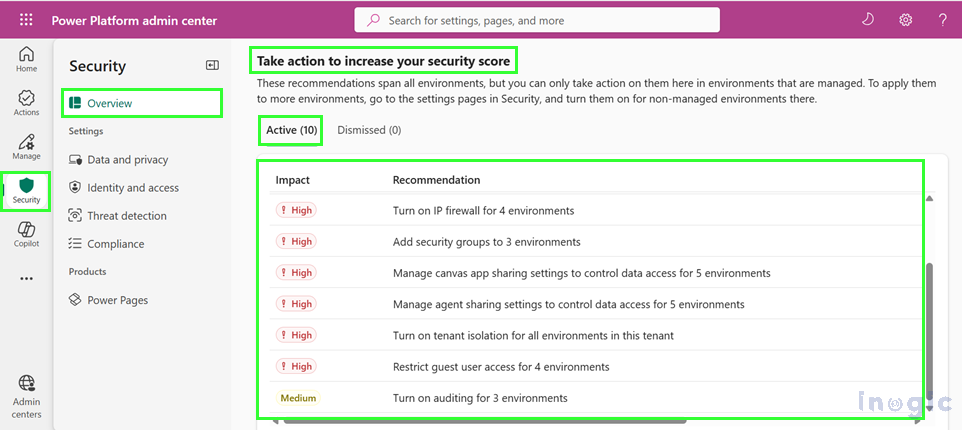
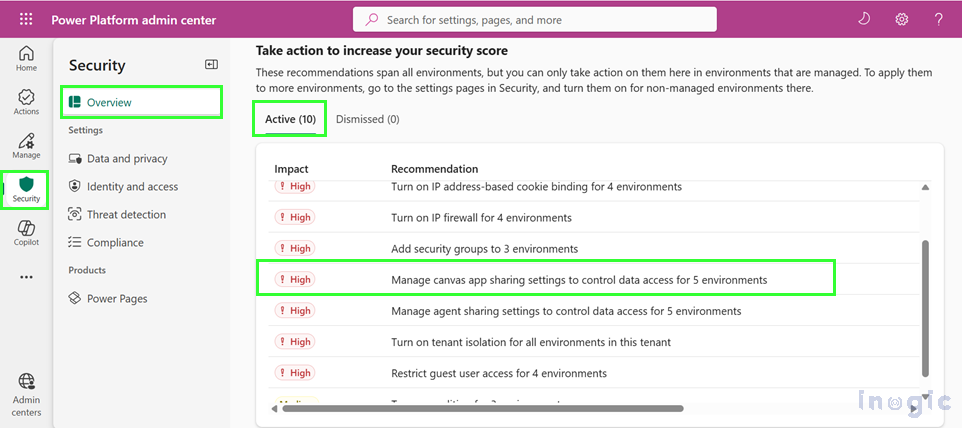
- Scroll to “Take action to increase your security score”
- Review recommendations in the Active tab
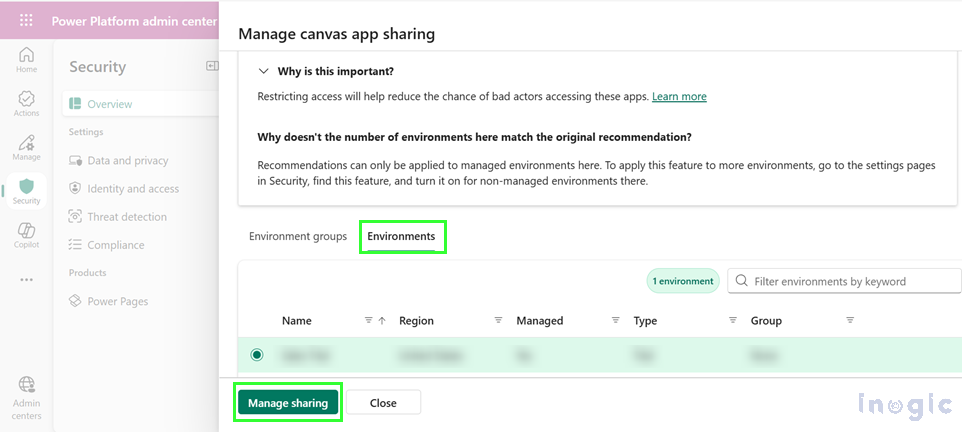
- Select environments from either the Environments tab (individual selection) or the Environment groups tab (bulk management)
- Click the action button (e.g., “Manage sharing,” “Configure IP firewall,” or “Configure auditing”)
Each recommendation shows the potential impact on your security score, helping you prioritize high-impact improvements.
Step 5: Manage Proactive Policies for Governance and Security
Power Platform offers three categories of proactive policies accessible through the Security Overview page:
Data Protection and Privacy
- Ensures personal information is securely handled and protected
- Prevents unauthorized data access
- Features: customer-managed keys, data policies, Azure Virtual Network
Identity and Access Management
- Ensures only authorized users access sensitive data
- Features: IP firewall, IP address-based cookie binding, tenant isolation, environment security groups, sharing controls, guest access restrictions
Compliance
- Implements robust compliance measures for regulatory adherence
- Features: Customer Lockbox, auditing
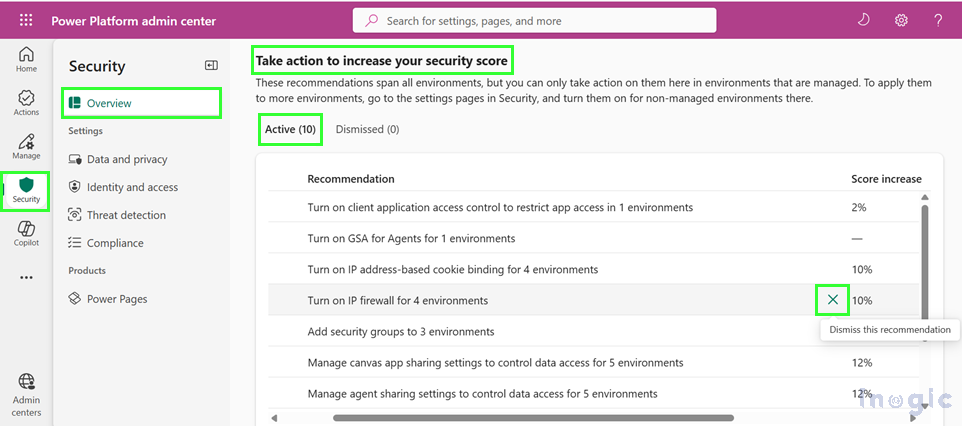
Step 6: Dismiss Recommendations When Mitigated
If you’ve addressed a security concern through alternative solutions outside Power Platform’s native controls, you can dismiss recommendations to reflect your actual security posture accurately.
To dismiss a recommendation, complete the following steps:
- Sign in to the Power Platform Admin Center.
- In the left navigation pane, select Security.
- Under the Security section, choose Overview.
- On the Overview page, scroll down to the Take action to increase your security score section.
- In the Active tab, locate and select the recommendations you want to dismiss.
- Click the X (dismiss) icon next to the selected recommendation.
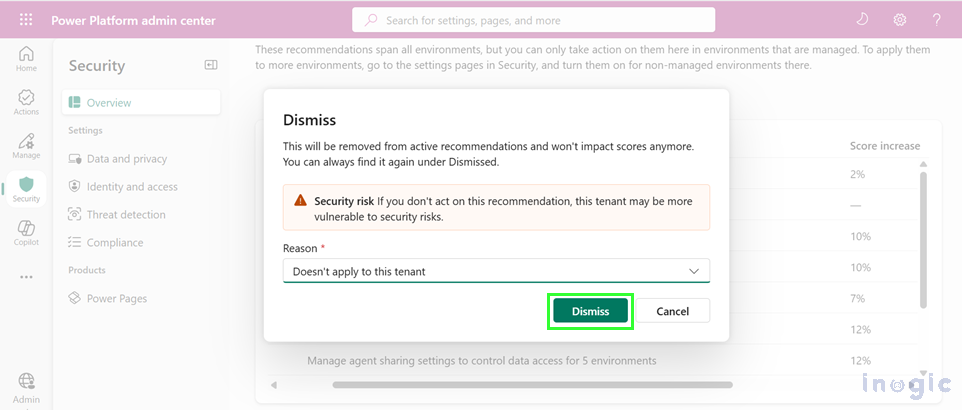
- A Dismiss window will appear. Choose a reason from the dropdown menu and select Dismiss.
The recommendation moves to the Dismissed tab.

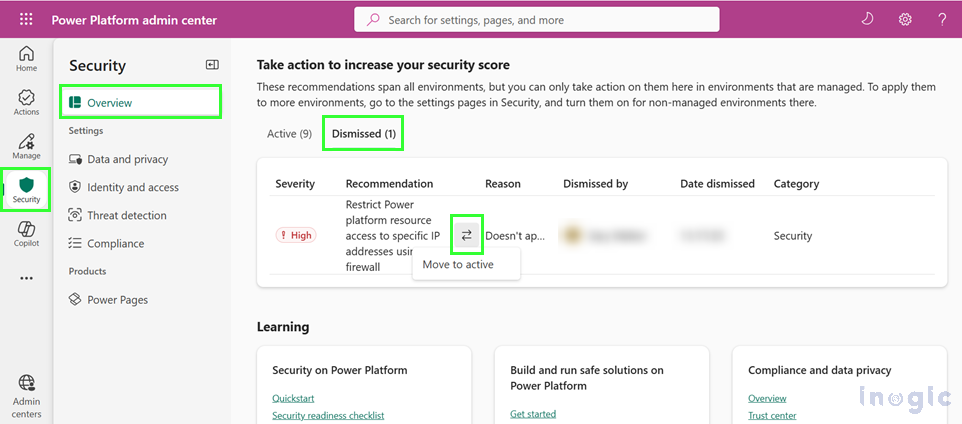
To reactivate a dismissed recommendation:
- Go to the Dismissed tab
- Select the recommendation
- Click the Arrows icon
The recommendation returns to the Active tab, allowing you to reconsider implementing the suggested control.
Step 7: Manage Security Settings at Environment Group Level
For organizations managing multiple environments at scale, configure security settings at the environment group level to ensure uniform enforcement across all environments in a group.
Currently available for:
- Sharing
- IP Firewall
- IP address-based cookie binding
To configure at the environment group level:
- Select a recommendation on the Security Overview page
- Choose the Environment groups tab
- Select specific environment groups or switch to the Environments tab for individual selection
- Click the management button (e.g., “Manage sharing”)
This streamlined approach simplifies administration and enhances security governance across both startups and enterprises.
SS>> highlight manage sharing recommendation from the SS below
FAQs: Power Platform Security Overview & CRM Data Protection
1. What is the Power Platform Security Overview page?
The Power Platform Security Overview page is a centralized dashboard in the Power Platform admin center that helps administrators monitor security posture, review security scores, and activate Microsoft-recommended controls. It provides visibility into risks, misconfigurations, and governance gaps across Dynamics 365 and Power Platform environments.
2. Why is the Security Overview important for Dynamics 365 CRM administrators?
CRM administrators rely on the Security Overview to track who is accessing customer data, identify apps or flows with unnecessary permissions, and ensure compliance with data protection policies. It helps prevent unauthorized data sharing and strengthens the overall security posture across all CRM-connected apps and environments.
3. How do I enable tenant-level analytics to view my Power Platform security score?
To view your security score, tenant-level analytics must be turned on. You can enable it from Power Platform Admin Center → Manage → Tenant Settings → Analytics → Tenant-level analytics → Save. It may take up to 24 hours for security data to appear.
4. What roles are required to access the Security Overview page?
You must be assigned either the Power Platform Administrator or Dynamics 365 Administrator role to access the Security Overview and view the security scorecard, recommendations, and tenant-wide insights.
5. How is the Power Platform security score calculated?
Your security score is calculated using the formula:
(Your score ÷ Total possible score) × 100.
Each enabled security feature adds points based on its scope and impact. The score updates every 24 hours and may change if Microsoft adds new security features.
6. What does a low, medium, or high security score mean?
- Low (0–50): High risk; many critical security features disabled
- Medium (51–80): Moderate protections enabled; improvement needed
- High (81–100): Strong security posture with most key features applied
Your goal is to raise your score by implementing recommended actions.
7. What are Managed Environments, and why should I enable them?
Managed Environments offer enhanced governance, data protection, analytics, and monitoring capabilities. Converting environments to managed mode strengthens security and ensures consistent policies across your tenant. Admins can convert multiple environments at once using the “Get enhanced security features” panel.
8. What triggers security recommendations in Power Platform?
Recommendations are triggered when Microsoft best practices are not met. Examples include:
- More than 10 admins in an environment
- Auditing turned off
- No tenant-level data policy
- No IP firewall configured
- Guest access not restricted
- Environments without security groups
- Tenant isolation disabled
These appear under “Take action to increase your security score.”
9. How do I implement recommended security actions?
From the Security Overview page, go to the Active recommendations tab, select an environment or environment group, and choose the relevant action (e.g., Configure IP firewall, Manage sharing, Configure auditing). Each action shows how much it will improve your security score.
10. Can I dismiss a recommendation if I’ve already resolved the issue externally?
Yes. If you addressed a risk outside Power Platform’s native controls, you can dismiss the recommendation. Simply open the Security Overview → Active tab → select the item → click the X → provide a reason → Dismiss. It will move to the Dismissed tab.
11. How can I manage security settings across multiple environments?
Power Platform allows managing certain settings, such as Sharing, IP Firewall, and IP address-based cookie binding, at the environment group level. This ensures consistent security across all environments in a group and simplifies administration for large organizations.
12. What types of policies can be managed from the Security Overview page?
You can manage three categories of proactive security policies:
- Data Protection & Privacy: Data policies, VNet, customer-managed keys
- Identity & Access Management: IP firewall, tenant isolation, security groups, guest access
- Compliance: Customer Lockbox, auditing
These help maintain regulatory compliance and strong identity controls.
13. How often should administrators review the Power Platform Security Overview?
Admins should review the Security Overview regularly, ideally weekly, to monitor score changes, apply new recommendations, convert unmanaged environments, and ensure ongoing compliance and protection of Dynamics 365 CRM data.
14. What happens if new security features are added by Microsoft?
When new features are introduced, the total possible score increases. This may lower your security percentage even if your settings haven’t changed, prompting you to implement new recommended features to maintain a high score.
Conclusion
The Power Platform Security Overview page is your essential tool for managing CRM security fundamentals. By regularly monitoring your security score, implementing recommended controls, and enabling Managed Environments, you create a secure foundation for your Dynamics 365 and Power Platform workloads.
Start today by accessing your security score, understanding your current posture, and taking your first action to improve security in your organization. Dismiss recommendations you’ve addressed through alternative means, manage policies at the environment group level for scale, and consistently work toward higher security scores. Regular attention to these fundamentals ensures your CRM data remains protected while your team works efficiently within a secure, governed environment.
The post Mastering Power Platform Security: A Complete Guide to Protecting Your CRM Data first appeared on Microsoft Dynamics 365 CRM Tips and Tricks.
Original Post https://www.inogic.com/blog/2025/11/mastering-power-platform-security-a-complete-guide-to-protecting-your-crm-data/